How It Works
Introduction
Our system combines secure technology and user-friendly tools to protect and manage your keys for secure operations like signing documents or logging in remotely. Here’s how it all fits together:
System Architecture
There are two main modes of operation: Offline Mode, where the solution uses Bluetooth to communicate with the middleware and enables mobile devices to use cryptographic keys; and Enterprise Mode, which includes additional functionalities required for compliance, auditing, and other essential operations.
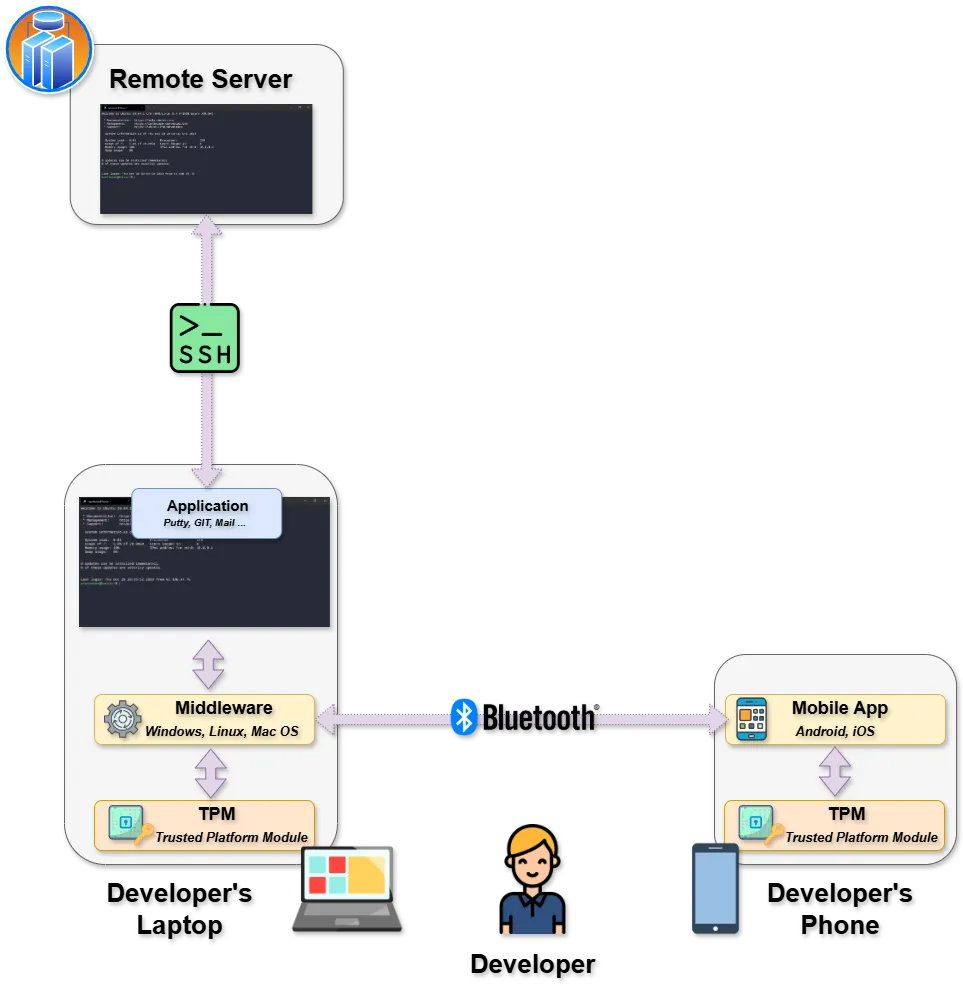
Offline only mode
The Offline-Only Mode is the open-source component, allowing users to generate keys offline and use the solution via Bluetooth.
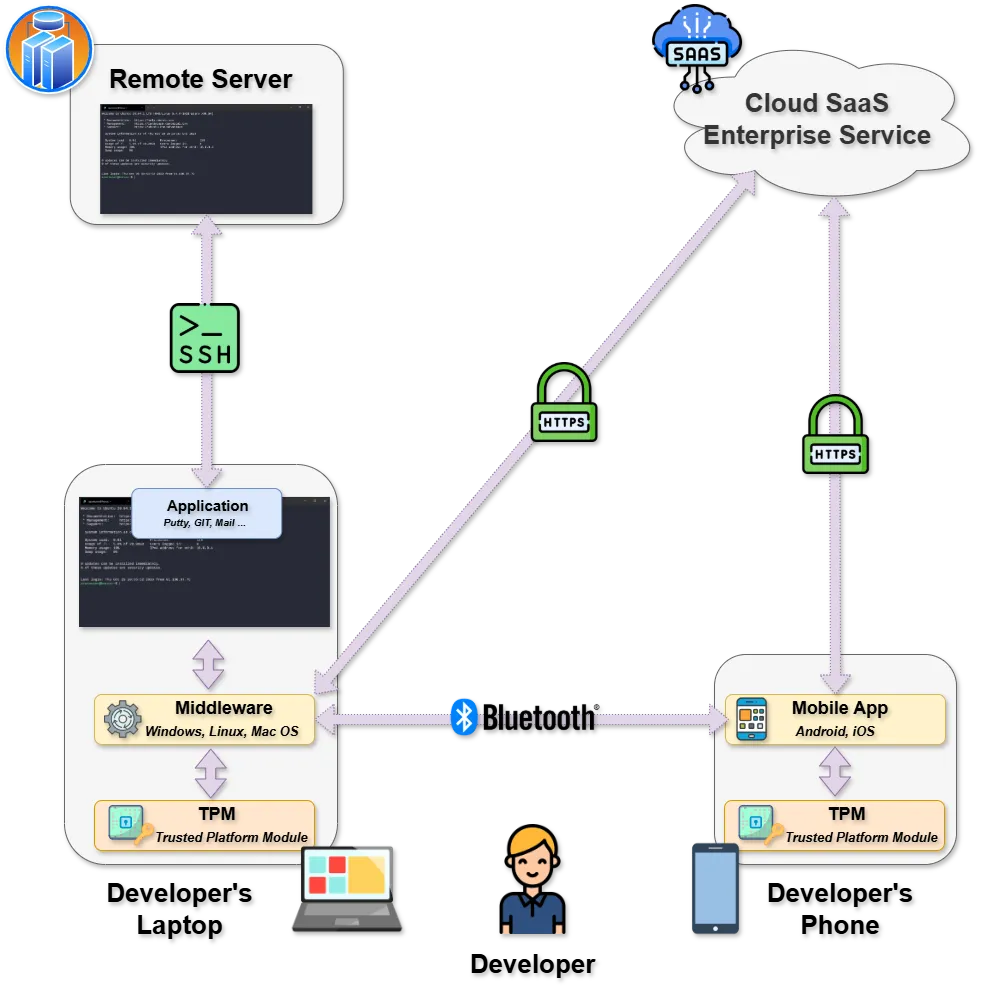
Enterpriese mode
Enterprise Mode requires an additional centralized SaaS solution to facilitate the management of multiple keys, provisioning, auditing, and compliance.
Smartphone
A standard smartphone running iOS or Android is the starting point. You’ll need access to the Play Store or App Store to install our app. This app manages your secure keys and connects to the rest of the system.
Secure Key
The “Secure Key” is the backbone of the system. It’s a cryptographic key (RSA or EC) stored in a secure area of your smartphone, like the Secure Enclave. Access to the key is tightly controlled—usually requiring biometric authentication (e.g., your fingerprint) or another secure unlocking method. Alternatively, keys can be stored in other secure devices like SmartCards or TPMs.
SaaS
Our cloud platform, or SaaS (Software as a Service), acts as the central hub. It connects your smartphone and secure keys to other parts of the system. SaaS also provides:
- Documentation and resources for users.
- Middleware downloads for different operating systems.
- Support pages.
- Account and company management.
- Auditing tools to track usage and ensure security.
Key Store
The Key Store is the smartphone app where your secure keys are stored and managed. It’s linked to your SaaS account for seamless integration with the rest of the system.
Middleware
Middleware is specialized software designed to let your computer work with secure keys. It supports key operations like signing, encrypting, or authenticating. Each operating system has its own version:
- Windows: Uses CNG.
- Linux: Uses PKCS#11.
- macOS: Likely uses its own cryptography API.
Middleware must be registered with the SaaS platform to enable secure key use. Once registered, you can perform actions like:
- Securely logging into a server (SSH).
- Signing a document.
- Any task involving cryptographic signatures or decryption.
Each instance of Middleware is uniquely identified using its own private cryptographic key, which proves its identity to the SaaS platform. For maximum security, these keys are ideally stored in hardware devices like TPMs.
Putting It All Together
You use the smartphone app to manage your secure keys. Middleware handles the cryptographic operations on your computer. The SaaS platform ties everything together, ensuring secure, seamless, and user-friendly operations.
This system provides a high level of security while remaining easy to use, ensuring your sensitive operations are always protected.